
static analysis - IDA search results not showing up in a separate window - Reverse Engineering Stack Exchange
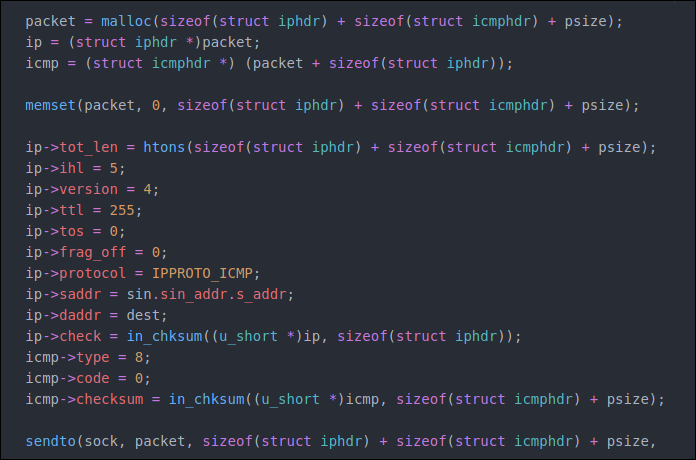
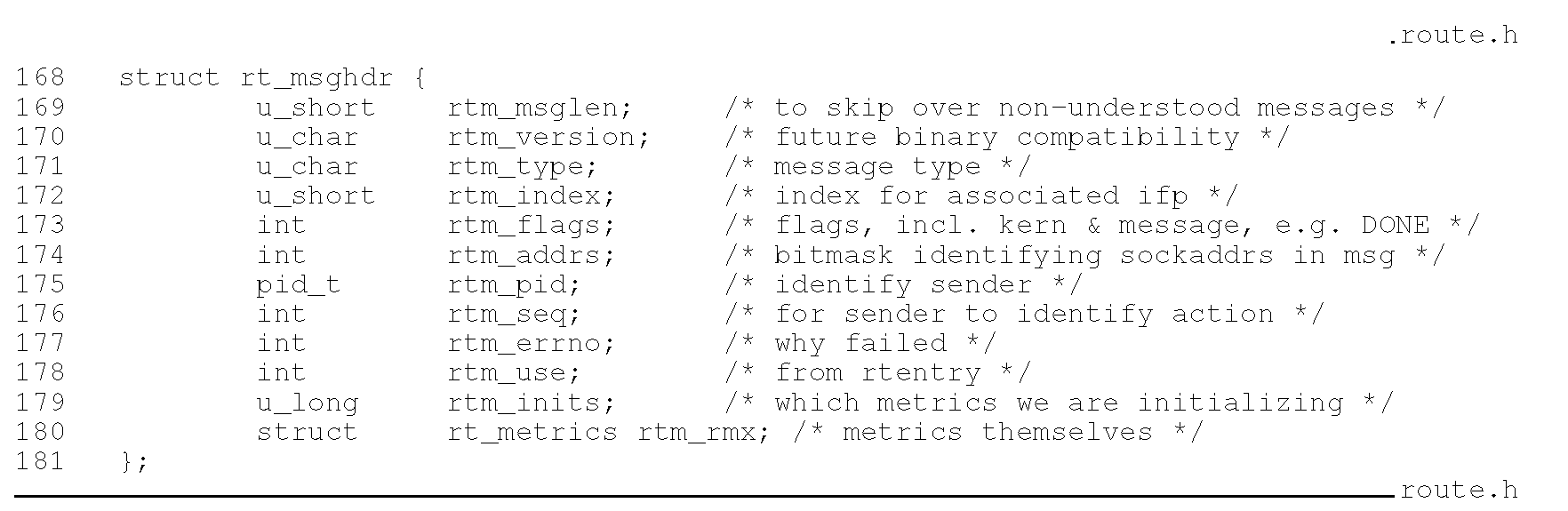
struct shmid_ds{ struct ipc_perm shm_perm; int shm_segsz; u_short shm_lpid; u_short shm_cpid; u_short shm_nattch; time_t shm_ati
![PDF] Providing process origin information to aid in computer forensic investigations | Semantic Scholar PDF] Providing process origin information to aid in computer forensic investigations | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4cbe681e892a6ee062c132c2587865bf2e7782c1/9-Figure2-1.png)
PDF] Providing process origin information to aid in computer forensic investigations | Semantic Scholar






![PDF] LASzip: Lossless Compression of Lidar Data | Semantic Scholar PDF] LASzip: Lossless Compression of Lidar Data | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3d59ab0bfc201ffdae77ca474b264b48e6d85fcc/2-TableI-1.png)



